Online Privacy
Your Face Belongs to Us</big<
Publisher: Penguin Random House
September 2023
Synopsis
The story of a small AI company that gave facial recognition to law enforcement, billionaires, and businesses, threatening to end privacy as we know it.
New York Times tech reporter Kashmir Hill was skeptical when she got a tip about a mysterious app called Clearview AI that claimed it could, with 99 percent accuracy, identify anyone based on just one snapshot of their face. The app could supposedly scan a face and, in just seconds, surface every detail of a person's online life: their name, social media profiles, friends and family members, home address, and photos that they might not have even known existed. If it was everything it claimed to be, it would be the ultimate surveillance tool, and it would open the door to everything from stalking to totalitarian state control. Could it be true?
Keywords: Artificial Intelligence (AI), psychometrics, biometrics, profiling, databanks
1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0
Surveillance Capitalism
Surveillance capitalism is an economic system centred around the commodification of personal data with the core purpose of profit-making. The concept of surveillance capitalism, as described by Shoshana Zuboff, arose as advertising companies, led by Google's AdWords, saw the possibilities of using personal data to target consumers more precisely.[1]
Collecting and processing data in the context of capitalism's core profit-making motive might present a danger to human liberty, autonomy and wellbeing. Capitalism has become focused on expanding the proportion of social life that is open to data collection and data processing. This may come with significant implications for vulnerability and control of society as well as for privacy.
Economic pressures of capitalism are driving the intensification of connection and monitoring online with spaces of social life becoming open to saturation by corporate actors, directed at the making of profit and/or the regulation of action. Therefore, personal data points increased in value after the possibilities of targeted advertising were known.
... the purchase of personal data points to the richest in society.
Keywords: Capitalism, privacy rights, surveillance, digital technologies, democracy, collective action, twenty-first-century society, social inequality, power, internet, surveillance capitalism
References: https://en.wikipedia.org/wiki/Surveillance_capitalism#References
See also:
Commercialization of the Internet - https://en.wikipedia.org/wiki/Commercialization_of_the_Internet
Criticism of capitalism - https://en.wikipedia.org/wiki/Criticism_of_capitalism
Data mining - https://en.wikipedia.org/wiki/Data_mining
Free and open-source software - https://en.wikipedia.org/wiki/Free_and_open-source_software
Mass surveillance industry - https://en.wikipedia.org/wiki/Mass_surveillance_industry
Surveillance § Corporate - https://en.wikipedia.org/wiki/Surveillance#Corporate
Targeted advertising - https://en.wikipedia.org/wiki/Targeted_advertising
Privacy concerns with social networking services - https://en.wikipedia.org/wiki/Privacy_concerns_with_social_networking_services
1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0
Surveillance State
- Inside China's Quest to Launch a New Era of Social Control
Author: Josh Chin and Liza Lin
Award-winning journalists Josh Chin and Liza Lin take readers on a journey through the new world China is building within its borders, and beyond. Telling harrowing stories of the people and families affected by the Party’s ambitions, Surveillance State reveals a future that is already underway—a new society engineered around the power of digital surveillance.
How has China democratized state surveillance around the globe?
The greatest barrier to the spread of state surveillance in the past has been money. Tracking large numbers of people required paying large numbers of people to spend countless hours operating expensive equipment. Much like they did with drones and telecom equipment, Chinese technology companies have made state-of-the-art surveillance systems affordable and accessible. They have also been happy to arrange favorable loans to governments interested in buying Chinese tracking technology. Research by Sheena Greitens at the University of Texas shows Chinese police surveillance systems being sold to more than 80 countries around the world, including several democracies. Chinese tech companies themselves say they have sold their products much more widely than that, though we haven’t been able to verify those claims.
1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0
Tips for Protecting Your Privacy Online
by Julia Angwin - 2014
In the course of writing her book, Dragnet Nation, Julia Angwin tried various strategies to help protect her privacy. Here, she shares some tips for readers, starting with how to build better passwords. Passwords are the first line of defense between your private data and an attacker – whether it is a criminal hacker or a spy agency. But most of the conventional wisdom about building passwords is terrible. People are often told they should change their passwords every three months; that their passwords should be made strong with multiple symbols and letters; and the passwords should not be written down anywhere.
Computer scientist Ross Anderson has summed up this terrible advice as “Choose a password you can’t remember, and don’t write it down.” Faced with that impossible task, most people use passwords that are easy to remember – the most popular password is still 123456 – and use it for every single account.
It’s actually better advice to choose a more secure password and write it down somewhere in a safe place. After all, it’s much less likely that someone will break into your house and steal your master password list than it is that someone will hack into your account from afar through a weak password.
However, even if you write down your passwords, you still face the difficult task of dreaming up the dozens of passwords that seem to be required for modern life. At first, I tried to make up my own passwords, but after I stumbled on this password-strength estimator, I realized that many of my homegrown passwords were still easy to crack. So, after much searching for a perfect password strategy, I came up with a two-tiered solution for building strong passwords:
• I used 1Password, a password management software that generates and store passwords, for less important accounts – such as my frequent flier and online shopping accounts. Like its competitors, KeePass, 1Password generates strong passwords from strings of letters, numbers and symbols and stores them on my machine in an encrypted file.
• I used a simple, low-tech passphrase-generating system called Diceware, for more important passwords – such as my e-mail and online bank accounts. It works like this: roll a six-sided die five times, then take the numbers you roll and match them up to the Diceware word list, which contains 7,776 short words. Repeat this five times and you will end up with a five-word passphrase that is hard for attackers to crack, but easy to remember.
HOW TO SAFELY BROWSE THE WEB
One of the easiest and simplest things you can do to protect your privacy is to be a smarter Web browser.
This is surprisingly difficult because most popular Web browsing software is set up to allow users to be tracked by default. The reason is simple economics – you don’t pay for Web browsing software, so the companies that make it have to find other ways to make money.
The most egregious example of this conflict came in 2008 when Microsoft’s advertising executives helped quash a plan by the engineers to build better privacy protections into the Internet Explorer 8 Web browser. Microsoft has since added additional protections – but they are not turned on by default. The situation is no better at Google, whose Chrome Web browser has a “buried and discouraged” the Do Not Track button, and is pioneering the use of new tracking technology that cannot be blocked. And it’s worth noting that the other big Web browser maker, Mozilla Corp., receives 85 percent of its revenues from its agreement to make Google the default search engine on Firefox. Even worse, many of the tools that Web browsers offer to protect privacy are not effective. Tracking companies have refused to honor the Do Not Track button. And Google Chrome’s Incognito mode and Internet Explorer’s InPrivate Browsing mode won’t protect you from being tracked. Those settings simply prevent other people who use your Web browser after you to see where you’ve been online.
And so, in order to prevent the most common types of tracking, I ended up loading up my Web browser – Mozilla’s Firefox – with a bunch of extra software. It sounds like a lot of work, but most of this software can be installed in a few minutes. Here’s what I used:
• I installed HTTPS Everywhere, created by the Electronic Frontier Foundation and the Tor Project. This tool forces your Web browser to use encrypted Internet connections to any website that will allow it. This prevents hackers – and the National Security Agency – from eavesdropping on your Internet connections.
• I installed Disconnect, a program created by former Google engineer Brian Kennish, which blocks advertisers and social networks, such as Facebook and Twitter, from tracking which websites you visit.
• I set my default search engine to be DuckDuckGo, a search engine that doesn’t store any of the information that is automatically transmitted by your computer — the IP address and other digital footprints — so DuckDuckGo has no way to link your search queries to you. That means DuckDuckGo won’t auto-complete your search queries based on your previous searches or based on your physical location, as Google does. So you’ll have to be a little smarter about your searches, and remember to bookmark the pages that you visit often, to save time.
After browsing with my ungainly setup for nearly a year, I found a Web browser that had all the features I wanted built in — called WhiteHat Aviator. It has built-in HTTPS Everywhere, it doesn’t retain or sell your online activity, and it uses Disconnect to block trackers from advertisers and social media companies. Its default search engine is DuckDuckGo.
It’s built by a computer security firm called WhiteHat Security, but it hasn’t been audited by any computer security experts yet, as far as I can tell. So use it at your own risk (and currently you can only use it on the Mac OSX operating system). But I’ve been using it for a few months, and after some bugginess in the beginning, I’ve started to enjoy the unusual feeling of having privacy as a default setting.
Courtesy of Julia Angwin
Copyright 2014, Julia Angwin
Another option that Angwin suggests for protecting your privacy online includes opting out from data brokers
□
Julia Angwin is an investigative journalist for ProPublica and former reporter for The Wall Street Journal. She is author of the new book, Dragnet Nation: A Quest for Privacy, Security and Freedom in a World of Relentless Surveillance
○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○
- More References
General Data Protection Regulation (GDPR)
https://en.wikipedia.org/wiki/General_Data_Protection_Regulation http://eur-lex.europa.eu/legal-content/EN/TXT/?uri=uriserv:OJ.L_.2016.119.01.0001.01.ENG
Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (Text with EEA relevance)
○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○ ○
GreenPolicy360 / Digital Rights Organizations
Digital Rights
- http://www.greenpolicy360.net/w/Digital_Rights
- http://www.greenpolicy360.net/w/Strategic_Policy-Internet_Online_Rights
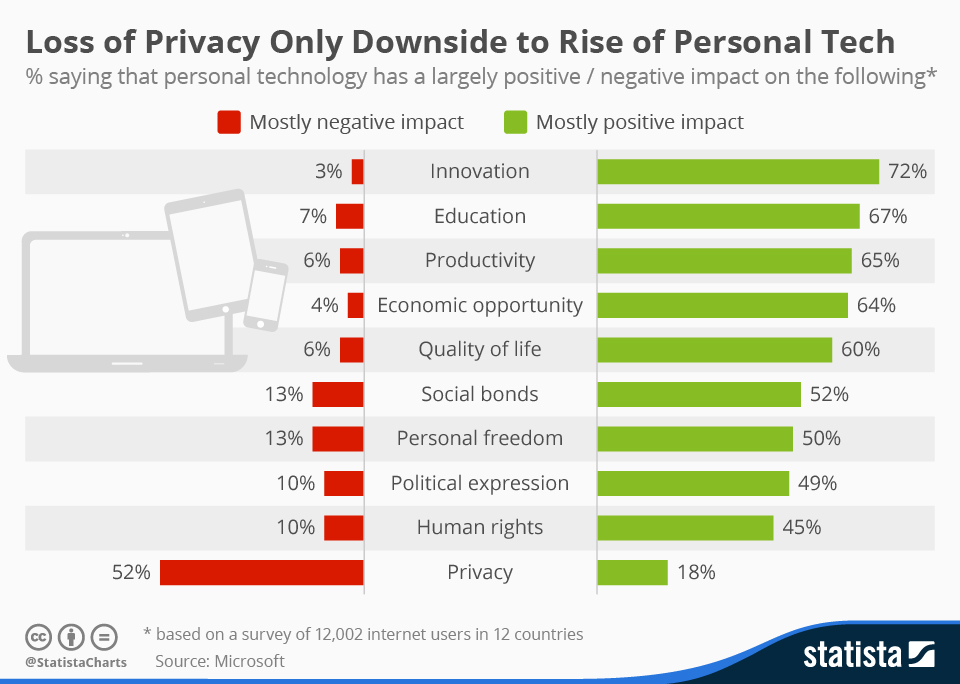
http://www.statista.com/chart/3148/loss-of-privacy-only-downside-to-rise-of-personal-tech/
Digital Privacy Issues -- via Reddit
Feb 23, 2015 - Reddit AMA / Citizenfour--Snowden-Greenwald-Poitras
Privacy Information via Wiki Community
Global surveillance disclosures, 2013-present -- via Wikipedia 1970-2013
Privacy concerns with social networking services -- via Wikipedia
Information privacy -- via Wikipedia
Online advertising -- via Wikipedia
FTC Fair Information Practice -- via Wikipedia
Fair Use and Data Mining -- via Wikipedia
Big Data, Online Advertising and Marketing
Electronic Frontier Foundation
○